Recycle2Cloud – migration services for physical servers and legacy applications to the cloud
In some respects cloud servers work in the same way as physical servers but the functions they provide can be very different. When opting for cloud hosting, clients are renting virtual server space rather than renting or purchasing physical servers. They are often paid for by the hour depending on the capacity required at any particular time.
Unlike dedicated servers, cloud servers can be run on a hypervisor. The role of a hypervisor is to control the capacity of operating systems so it is allocated where needed. With cloud hosting there are multiple cloud servers which are available to each particular client. This allows computing resource to be dedicated to a particular client if and when it is necessary. Where there is a spike in traffic, additional capacity will be temporarily accessed by a website, for example, until it is no longer required. Cloud servers also offer more redundancy. If one server fails, others will take its place.
Below are the key benefits of cloud servers:
- Flexibility and scalability; extra resource can be accessed as and when required
- Cost-effectiveness; whilst being available when needed, clients only pay for what they are using at a particular time
- Ease of set up; Cloud servers do not require much initial setup
- Reliability; due to the number of available servers, if there are problems with some, the resource will be shifted so that clients are unaffected.
Essentially, all cloud applications must be “Service Consumable” – that is, they can be accessed as a service. Additionally, a cloud application must have at least unit tenancy where it can provide segregation between individual end users. Once these base qualities are met, cloud applications can then mix any of the 3 sub-types for a composite architecture that defines that cloud application’s total architectural foundation. The 3 sub-types are best understood as follows:
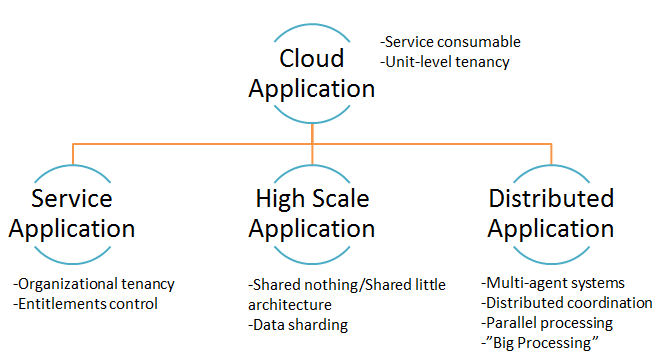
- Service Applications – Applications whose architecture up-level the service consumption model away from individual end users and into an architecture that groups users together and can segregate data and execution among groups, but share that data and execution within a group. We typically refer to these as a ‘SaaS’ apps but I’m avoiding using this term because it has certain implications that don’t make sense in the context of internal enterprise apps (where this sort of architecture has tremendous applicability).
- High scale applications – Applications whose architectures focus on achieving extreme levels of scale, needing to support high levels of concurrent access without compromise. Architectures rely on shared nothing models, data sharding, etc. to achieve this.
- Distributed applications – Applications that typical deal with large amounts of data or complex analytic requests that require parallel computation or divide and conquer models. In these architectures, multiple agents in a distributed topology coordinate and act against a common problem to derive a solution. Things like map/reduce and monte carlo experiments fall into this category.
Securing Applications and Data in the cloud with Containers
As customers transition their applications and data to the cloud, it is critical for them to maintain, or preferably surpass, the level of security they had in their traditional IT environment. This section provides a prescriptive series of steps for cloud customers to evaluate and manage the security of their use of cloud services, with the goal of mitigating risk and delivering an appropriate level of support. The following steps will be discussed in detail below:
- Ensure effective governance, risk and compliance processes exist
- Audit operational and business processes
- Manage people, roles and identities
- Ensure proper protection of data and information
- Enforce privacy policies
- Assess the security provisions for cloud applications
- Ensure cloud networks and connections are secure
- Evaluate security controls on physical infrastructure and facilities
- Manage security terms in the cloud service agreement
- Deploy applications and data in isolated and secure containers
Cloud Application Integration
The growth in SaaS adoption, mobile applications, and the explosion of APIs has caused an outburst of endpoints, resulting in fragmentation of the enterprise. Companies are moving to the cloud as vital data is no longer stored exclusively on-premises. The challenge of interoperability between different devices and platforms has complicated matters for businesses, as it is difficult to connect dynamic applications, services, and data. Cloud computing helps businesses address their current integration challenges, while giving them the scalability, manageability, and reliability they need for the future.
Previously, companies have employed integration solutions from a single vendor. This approach, although unifying, causes complications as the platform or software might not be compatible with third party applications that the business may want to employ. Moreover, it constrains companies to integration products and tools from a single vendor, forcing them to work with applications that might not be finest solutions. As a result, many organizations have shifted from buying applications from a single vendor, and instead have employed a best of “breed approach”, mixing and matching vendors in order to obtain the best products for specific areas of business.
This best of breed approach allows businesses to employ specific applications to run the functional areas of their business (payroll, invoicing, e-commerce, HR, CRM, ERP, marketing, etc.) and it is essential that each of the individual applications talk to each other. Information needs to shared across applications whether they reside on-premises or in the cloud in order for business processes to run smoothly. Without seamless communication between applications and services, business processes slow down, ultimately slowing down their time to live. Moreover, without a system to enable sharing of information, data remains within each application or database, creating information silos that prevent sharing if information and intelligence to other aspects of the business. Applications hosted as clustered containers can interoperate securely while delivering superior performance.
Based on innovative technology, our cloud hosting platform is ultra fast, autoscalable and allows you to customize your plan. It comes with VIP support. Whether you are starting a small development project or need to host a high-traffic enterprise site, your best managed containerized cloud hosting option is here.
Optimizing Cloud Hosting cost and Performance
Scalability is the best solution to increasing and maintaining application performance in cloud computing environments. Cloud computing vendors often resort to brute-force horizontal scaling by adding more physical or virtual machines, but this approach may not only waste resources but also not entirely solve performance issues, especially those related to disk and network I/O. In addition, customers and vendors alike have practical limits on their ability to scale, primarily constrained by costs and human resources. Smart application development can alleviate performance issues in many cases by isolating resource-intensive processes and assigning the appropriate assets to handle the load. However, for the most part scaling to meet performance demands remains a manual process and requires vigilant monitoring and real-time response. Change is the only constant when comparing cloud services offering and prices.
With years of hosting experience we can identify on an ongoing basis, the best and most cost effective cloud hosting solution on the month to month basis as per your critical parameters such as performance, latency, bandwidth, scalability, reliability, technology, energy efficiency and any other special requirements to be considered.
